NETWORK ATTENTATION AND TRUSTED COMPUTING-SPRINGROLE

Attestor can be defined as a person who attests to the genuineness of a document or signature by adding their own signature.
In today’s world there has been some major trends that have been immensely influential in the computing environment. The first that I would like to talk about is heterogeneity. We use to compute using everything from small cell phones, to handhelds, to desktop workstations, to rack-mounted servers and all the aforementioned need to inter-operate. This in one way or the other has led to widespread acceptance of open protocols for communication and portable language runtimes (such as Java and net virtual machines for programs performance.
The second major trend is mobility. Not only must all these varied computing devices inter-operate seamlessly, we must also be able to use most of our familiar programs and data across all of them. Both of these have significantly increased the importance of having a so-called ``common platform''. This common platform is increasingly the language runtime, that executes some form of platform-independent mobile code.
One way to get security assurances is to use closed systems. They enforce compliance with a certain security policy by being tightly controlled. They are usually manufactured by a single vendor to rigid specifications. Designers have complete control over the whole system and build it specifically to conform to a given security policy. When one closed system communicates with another, it knows within very tight bounds the expected behavior of the remote party. Common examples of closed systems are automated teller machines (ATMs) and proprietary game consoles
Open systems, on the other hand, have no central arbiter. Commodity personal computers and handhelds are examples of open systems. An open system can be easily changed to behave maliciously towards other systems that communicate with it. Two communicating open systems cannot assume anything about each others' behavior, and must be conservative in their assumptions.
Open systems, on the other hand, have no central arbiter. Commodity personal computers and handhelds are examples of open systems. An open system can be easily changed to behave maliciously towards other systems that communicate with it. Two communicating open systems cannot assume anything about each others' behavior, and must be conservative in their assumptions.
Taking into consideration the afore mentioned challenges, project springrole foundation is coming on board with some set of rules and regulations for a true evidence based status network with some gifts to individuals and witnesses. For such an initiative to occur, springhole Token enables the functionality of the set of rules and regulations. When we consider the usage of the system, most users interact with the system and others using the spring Token.
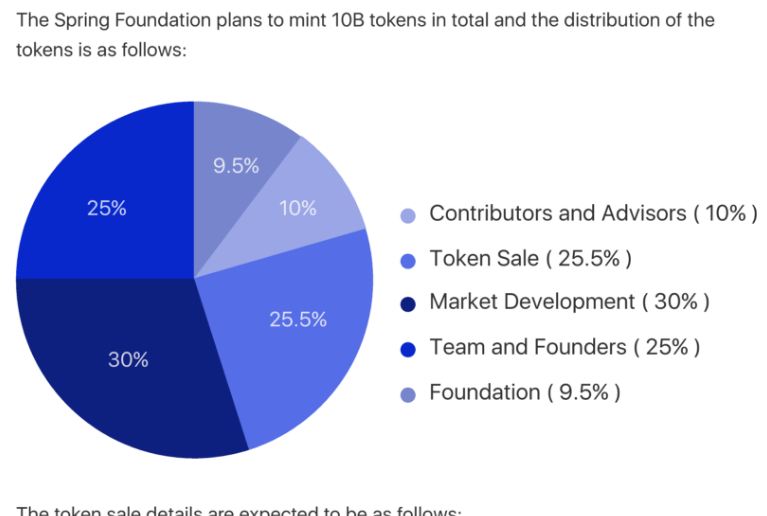
TOKEN SALES
TEAM MEMBERS



ADVISORS



READ MORE ON US
▪️Website: https://springrole.com/
▪️Whitepaper: https://docsend.com/view/k5nghff
▪️Telegram Announcements: https://t.me/springrole_announcements
▪️Press: https://docs.google.com/spreadsheets/d/1gIL3d4otUY5seneTdbtJ0ClrVmUeoyMSXPDpxi-lWII/edit#gid=0
▪️BitcoinTalk: https://bitcointalk.org/index.php?topic=3556999
▪️BitcoinTalk Bounty: https://bitcointalk.org/index.php?topic=3602729
▪️Telegram Bounty Group: https://t.me/joinchat/H58cR03LDuB9LFlobwVDIg
▪️Medium blog: https://blog.springrole.com
▪️Reddit: https://www.reddit.com/r/SpringRole/
▪️Twitter: https://twitter.com/SpringRoleinc
▪️Telegram Announcements: https://t.me/springrole_announcements
▪️Youtube: https://www.youtube.com/channel/UC7jYeZWJHhsV_2266gVMsZw
▪️Facebook: https://www.facebook.com/springrole/
▪️Website: https://springrole.com/
▪️Whitepaper: https://docsend.com/view/k5nghff
▪️Telegram Announcements: https://t.me/springrole_announcements
▪️Press: https://docs.google.com/spreadsheets/d/1gIL3d4otUY5seneTdbtJ0ClrVmUeoyMSXPDpxi-lWII/edit#gid=0
▪️BitcoinTalk: https://bitcointalk.org/index.php?topic=3556999
▪️BitcoinTalk Bounty: https://bitcointalk.org/index.php?topic=3602729
▪️Telegram Bounty Group: https://t.me/joinchat/H58cR03LDuB9LFlobwVDIg
▪️Medium blog: https://blog.springrole.com
▪️Reddit: https://www.reddit.com/r/SpringRole/
▪️Twitter: https://twitter.com/SpringRoleinc
▪️Telegram Announcements: https://t.me/springrole_announcements
▪️Youtube: https://www.youtube.com/channel/UC7jYeZWJHhsV_2266gVMsZw
▪️Facebook: https://www.facebook.com/springrole/
Author: Rastafarian
Ethereum wallet: 0xCA428804454488D46367631FC0D0De306852F3F3
Ethereum wallet: 0xCA428804454488D46367631FC0D0De306852F3F3
Comments
Post a Comment